
That's because Adobe engineers used reversible encryption to scramble the passwords contained in a 9.3-gigabyte file that's now available online. Surprisingly, they flouted almost universally recognized best practices that call for stored passwords to be protected by bcrypt or another one-way cryptographic hashing algorithm. Just as ground hamburger can't be converted back into steak, there's no mathematical way to reverse cryptographic hashes and return them to their plaintext origins. One-way hashing is designed to thwart cracking by requiring crackers to pass individual password guesses through the same algorithm and see if it produces the same long string of random-looking characters. When done correctly, it can take centuries to decipher long lists of credentials.
That's not at all the way the passwords for the 130 million active and inactive Adobe accounts are protected. They were scrambled using standard symmetric encryption. If crackers are able to figure out the key or keys that encrypt the data, they will have instant access to every single plaintext user password in the list.
To be sure, breaking the encryption is by no means a sure thing. The passwords are protected with the Triple DES encryption cipher. Depending on the keying option Adobe engineers chose, there could be from 256 to 2168 possible keys to be exhausted in a brute-force crack. Hackers can sometimes reduce the entropy by using meet-in-the-middle, chosen plaintext, or known plaintext attacks.
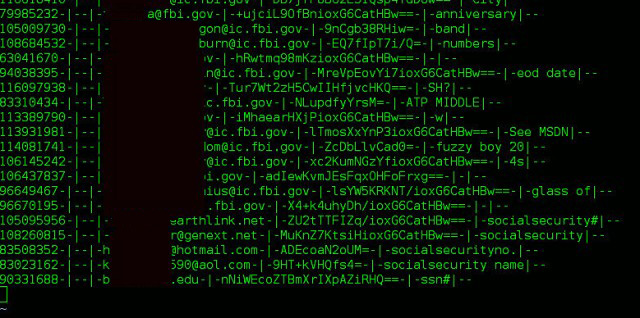
Then again, deciphering the file is by no means out of the question. In this case, attackers may have the advantage. The passwords, according to password expert Steve "Sc00bz" Thomas, are encrypted in a mode known as ECB. That was a poor choice on the part of Adobe engineers, because ECB often leaks information about the passwords, such as their last few characters and some of their lengths. In certain cases, for example, passwords that end in "e" will generate an encrypted string that ends in "n2auThm2+Q=="; those that are nine or 17 characters long will sometimes end in "mfZq5OGbb5".
Ticking time bomb
Whitehat researchers are still in the process of evaluating the file and assessing their chances of decrypting the passwords. No doubt, blackhats are doing the same thing. It's too early to say how much success either camp will have. One factor in their favor: the plaintext for many of the encrypted passwords is already known, since they were chosen by some of the same people trying to crack the encryption.
Indeed, the file shows encrypted credentials for a variety of well-known password crackers, including Thomas, Jeremi Gosney, and Per Thorsheim. With 130 million entries, it won't be hard for most whitehats and blackhats alike to know someone personally affected. At the very least, knowing one or more of the plaintext passwords ahead of time means attackers will know instantly when they've guessed the right key, because it will convert one or more of the encrypted passwords into the known cleartext.
Absent a major mistake on the part of Adobe, I'd wager outsiders probably won't be able to decrypt the file, given the difficulty of brute-forcing a Triple DES key. That would be good news. Gosney, a password security expert with Stricture Consulting Group, told Ars that of the 130 million encrypted passwords, 56 million of them are unique. A crack that, in one stroke, unleashed that many plaintext passcodes into the wild would be unprecedented, because a large percentage of people reuse the same or only slightly modified passcode over and over. The biggest single leak to date came in 2009 with the compromise of gaming website RockYou. It forever changed the password-cracking landscape by seeding it with a corpus of 32 million passcodes, 14 million of which were unique.
Even if the Adobe passwords can't be cracked, there's no guarantee that the people who accessed and dumped the file didn't obtain the encryption key or keys. Indeed, Gosney said, the Adobe intruders also leaked a file online showing they accessed Adobe's sensitive LDAP directory containing cell phone numbers and other contact details for company executives and employees. Given that level of entry, it's plausible the trespassers also stole the cryptographic keys and have already decrypted the passwords. Just because they didn't publish the key doesn't mean they don't have it.
What is clear is that Adobe never should have stored passwords in a reversibly encrypted format. Company officials seemed to acknowledge that. In a statement to Ars, Adobe spokeswoman Heather Edell wrote:
For more than a year, Adobe’s authentication system has cryptographically hashed customer passwords using the SHA-256 algorithm, including salting the passwords and iterating the hash more than 1,000 times. This system was not the subject of the attack we publicly disclosed on October 3, 2013. The authentication system involved in the attack was a backup system and was designated to be decommissioned. The system involved in the attack used Triple DES encryption to protect all password information stored. We currently have no indication of unauthorized activity on any Adobe ID account involved in the incident.
Translation: there's every indication that the new system follows best practices, because it uses a slow, one-way hashing function that's augmented by cryptographic salt. The breach and the leaking of the backup system graphically demonstrate how those sound decisions can be undone.
In all, the leaked file contains more than 150 million records, 130 million of which contain an encrypted password. Edell said that 38 million of the records are for active customer accounts. With hundreds of millions of live e-mail addresses to domains in government agencies and private industry, the file no doubt will also prove a boon to phishers and spammers. More details about the files are available here, although not all of the information contained there can be independently verified.
As Ars has explained before, the effectiveness of password cracking snowballs with each passing database breach. It's too early to say this file will be decrypted, but given the stakes, this cautionary tale surely shows how Adobe made an epic blunder.
reader comments
94